Hack the Box Experience
How to prepare a white-box hacking workshop and live happily ever after
After the successful experience of having a code challenge in March 2024, we decided to go further in delivering experiences to our colleagues.
Scouting around, I turned to Alessio Giorgianni, a developer with a passion for white hat hacking competition. We agree to try an experience using a platform called Hack the Box. Hack the Box Academy offers lots of information and training about IT Security and, in our case, some exercises we can use for hacking dummy applications, with a whitebox example (i.e., an example where all the code is undisclosed to us. There are also different kind of pentest). We agreed upon using a non-trivial quest, called Jerrytok. Jerrytok is a WAPT (Web App Penetration Testing) whitebox challenge. We got a simple web-application, written in PHP, which disclose the harm of using template engines in a not-proper way. It’s a good introduction to SSTI, Server Side Template Injection.
 Please wear your favorite hacker hoodie before trying the workshop
Please wear your favorite hacker hoodie before trying the workshop
Preparing the workshop
 Topics we focused on
Topics we focused on
Let’s not fool ourselves: hacking an application is not a trivial task. It requires a fond knowledge of how the application works, while we must use several tools to diagnose and to break the application. Preparing all this stuff requires quite a lot of time.
So, we prepared a virtual machine with all the needed tools. We tried to create a lightweight yet simple to prepare VM, so we started from a Debian 11 VM, in which we installed:
- a decoder and repeater, we used Burp Suite community edition
- a simple proxy, we used FoxyProxy
- a reverse proxy, we used ngrok
On to the job!
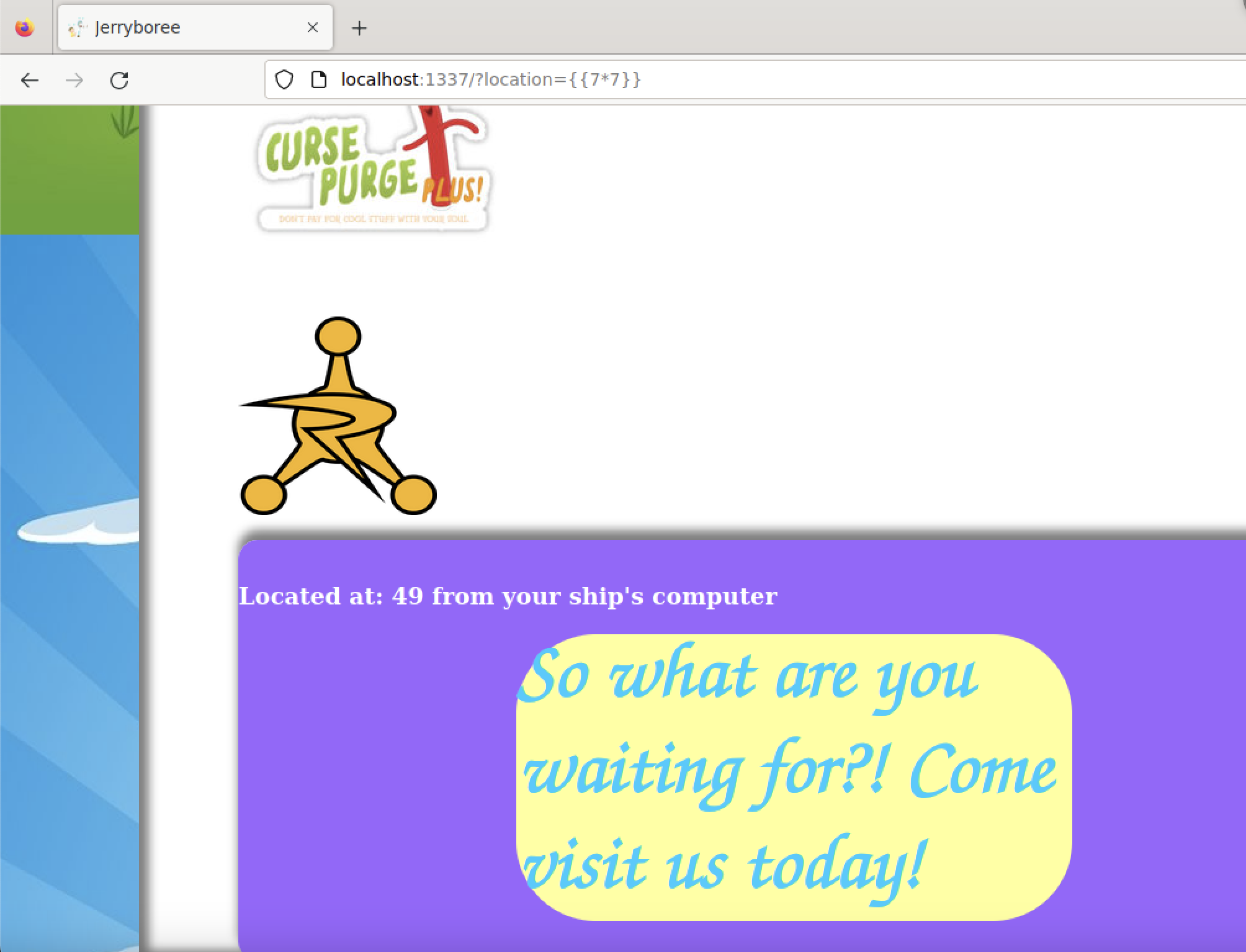 Vulnerability discovered! Can you guess how?
Vulnerability discovered! Can you guess how?
The workshop itself was divided into:
- a theoretical introduction to SSTI
- hands on the machine
During the introduction, we discovered what an SSTI is, which tools we need to control if a page can be affected by this problem and how to mitigate it. Alessio guided the hands-on exercise while some volunteers shared their screens to have feedback directly from the learners. The machine used a basic security system, so hacking is not trivial (even if it’s white-box).
Jerrytok, out!
Overall, it was a though yet interesting experience. It costs a little bit of effort preparing all the VM and the challenge, but attendees seemed to like it and we had a lot of discussion and curiosity about how the Alessio’s hack works.
The overview of Venerdì Protetto is available here.

Share this post
X
Facebook
Reddit
LinkedIn
StumbleUpon
Pinterest
Email